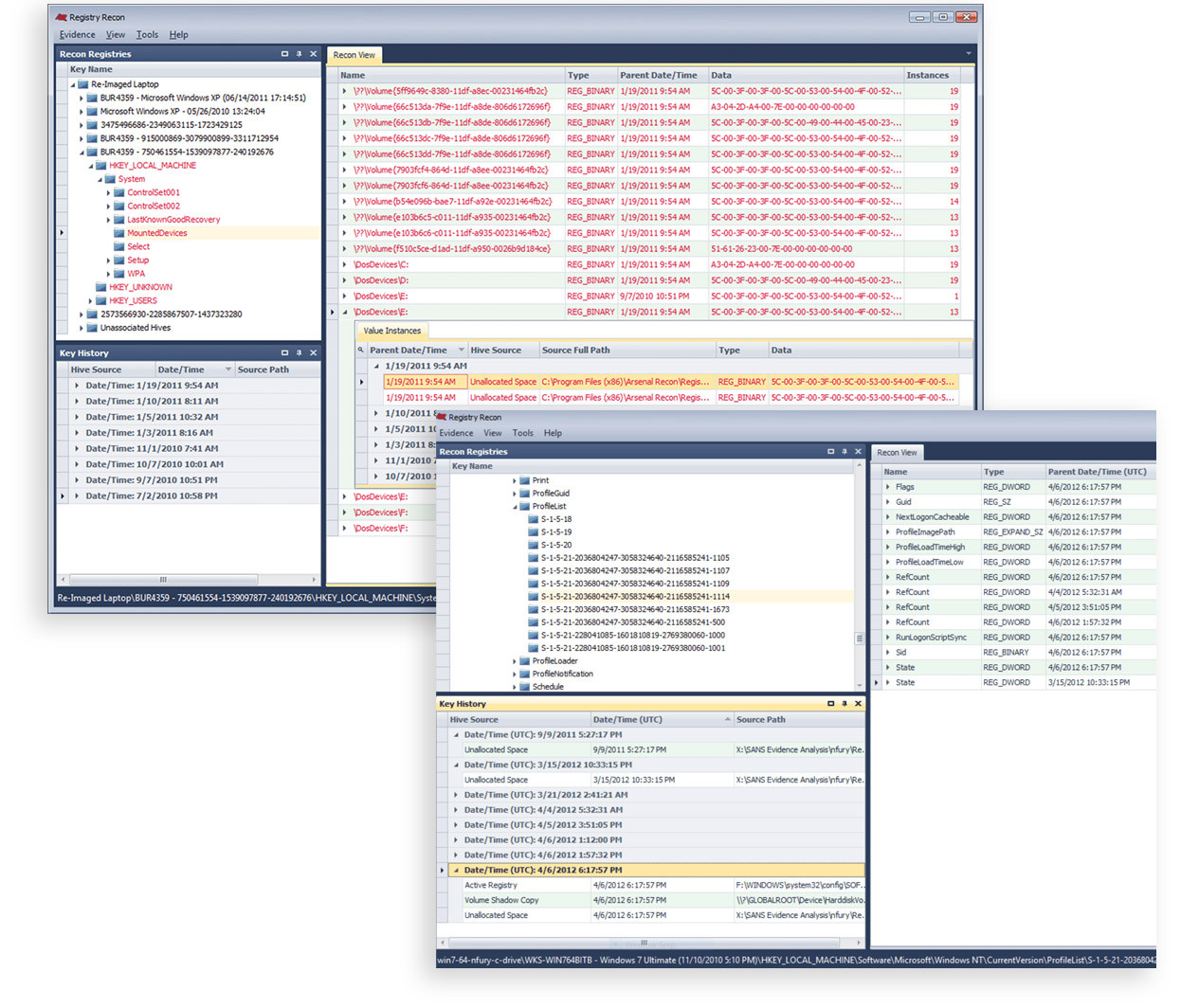
Registry forensics has long been relegated to analyzing only readily accessible Windows® Registries, often one at a time, in a needlessly time-consuming and archaic way. Registry Recon is not just another Registry parser. Arsenal developed powerful new methods to parse Registry data so that Registries which have existed on a Windows system over time can be rebuilt, providing unique insight into how Registry data has changed over time. Registry Recon provides access to an enormous volume of Registry data which has been effectively deleted, whether that deletion occurred due to benign system activity, malfeasance by a user, or even re-imaging by IT personnel.
Unlock the potential of huge volumes of Windows Registry data and see how Registries changed over time.