AMPED AUTHENTICATE
Photo and video analysis and tampering detection
The complete software for unveiling the processing history of a digital image or video.
Integrity verification
Verify the integrity of image and video files.
Processing analysis
Identify the processing history of photos and videos.
Tampering and deepfake detection
Detect tampered areas to determine their authenticity.
Camera identification
Identify the device used to capture images and videos.
Photo and video analysis and tampering detection
Unveil the processing history of a digital image
Every processing step in the life cycle of an image leaves some distinctive traces in the media. Visual content and metadata can today be easily manipulated to create credible fakes. The image mode in Amped Authenticate provides a suite of powerful tools to leverage these traces and localize manipulated regions, determine whether a media is an unaltered original, an original generated by a specific device, or the result of manipulation using editing software, making its admissibility as evidence questionable in legal proceedings.
Unveil the processing history of a digital video
The video mode in Amped Authenticate is a considerable advancement in video authentication. Within Amped Authenticate, it is a separate analysis mode dedicated entirely to videos. With the video mode, users can cover various video authentication steps, such as detecting inconsistencies, identifying the source device, examining coding details down to the macroblock level, and more. It also includes features such as visual inspection, export of processed videos, integration with the image mode, and the Advanced File Info tool.
Forensically sound
Courtroom admissible
Accurate | Repeatable | Reproducible
Produce a customizable forensic report ensuring that your results are well explained and reproducible. Without solid ways to validate that the information is accurate, digital images and videos could pose issues when they are presented as evidence in a case and in court. Therefore, thoroughly investigating an image and ensuring its trustworthiness and source is critical in today’s investigations.
Validated
For every filter in Amped Authenticate, you’ll find bibliographic references in the user manual and, whenever the filter is used, in the generated report. Authenticate contains image and video authentication filters based on tens of scientific papers and studies. When we implement a filter we carry out an experimental validation to check the performance reported in the literature are matched.
Image and video authentication
Amped Authenticate helps video analysts answer the many challenges of authenticity and integrity surrounding today’s digital images and videos.
Features
- 40+ tools and filters
Powerful image and video tools aid in the entire authentication workflow, from integrity analysis to content tampering analysis and deepfake detection. - Customizable
Batch processing, customizable configurations, and optional post-processing parameters create a powerful environment to boost your workflow. - Ballistics
Image ballistic tools allow you to verify which camera was used to shoot specific content, even if it has been scaled, cropped, or re-saved. - OSINT focused
Access powerful resources on the web for carrying out reverse image search, cross-checking image location and Sun position, and retrieving reference images for integrity analysis. - Comparison
Compare the results of two images side by side to understand where and how an image has been modified. - Compatible
Support for any standard image (JPEG, TIFF, BMP, PNG, HEIF, …) and video formats as well as RAW formats from many digital cameras. Extract images embedded in PDF and other formats. - Top-level customer support
Users can submit files and questions to Amped technical support when they need assistance with a specific filter or processing feature.
Used by
It is used by digital forensic experts and intelligence agencies worldwide.
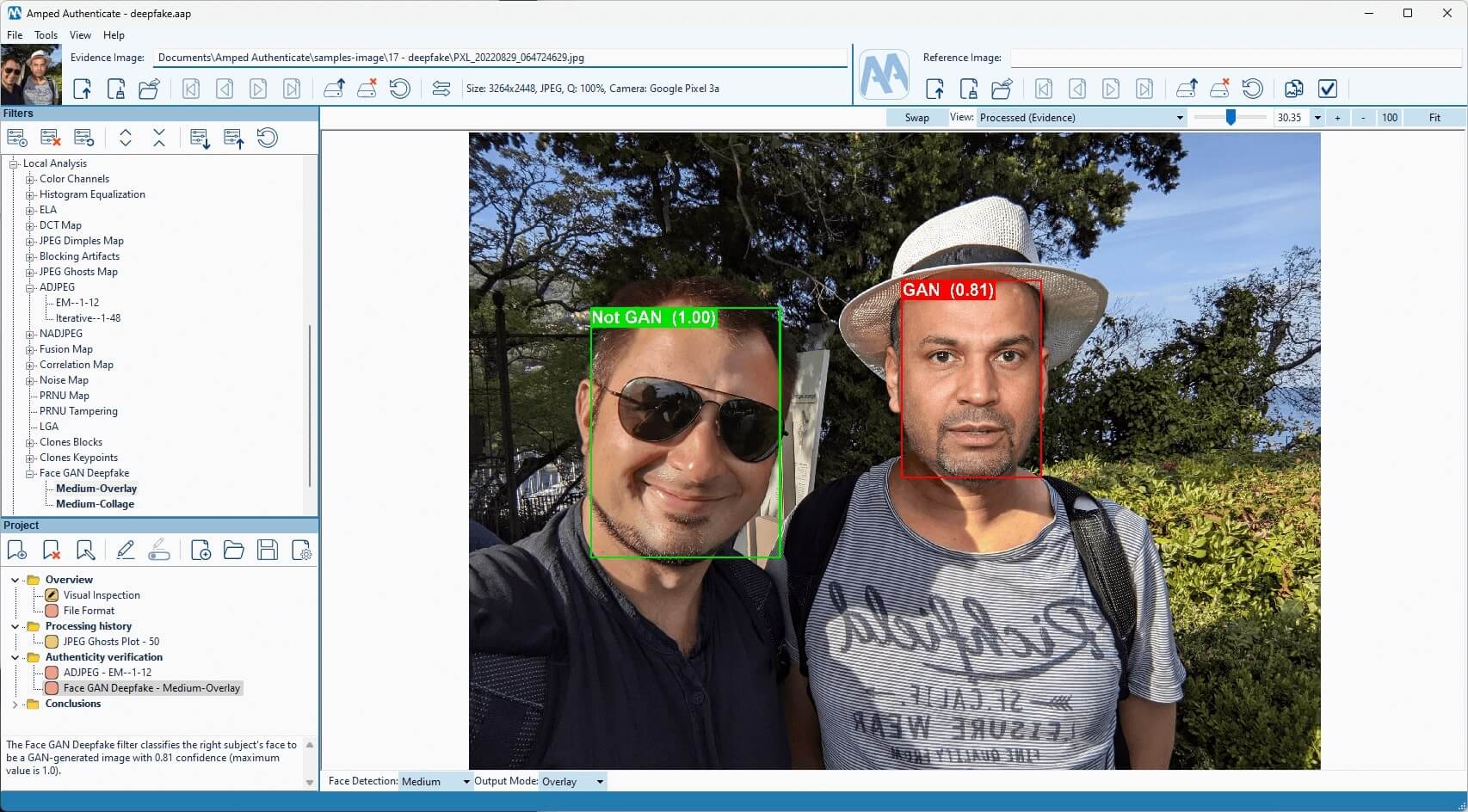
The Face GAN Deepfake filter in Amped Authenticate
Analyze images and videos
The Face GAN Deepfake filter first localizes faces within the image and then uses AI to classify each face and provide you with a label and a confidence score between 0 and 1. When the confidence score is above 0.8, the label can either be Real (green color) or Fake (red color).
When the score is lower, Authenticate will play it safer and write Uncertain Real or Uncertain Fake.