
Reliable.
Powerful. Trusted.
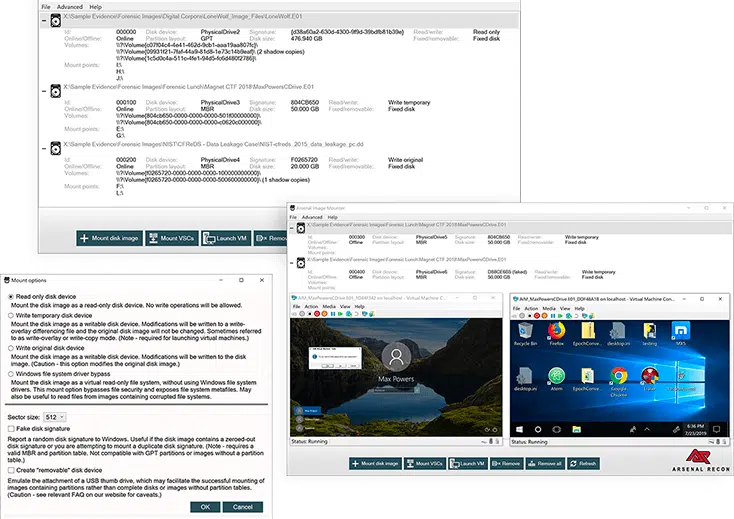
We are excited to announce that Arsenal Image Mounter will be replacing CARBON by SUMURI and is now available for purchase. Arsenal Image Mounter is a disk image mounting solution that allows users to mount the contents of disk images as complete disks in Windows, which is not possible with many other disk image mounting solutions. It also provides features such as integration with Disk Manager, launching virtual machines, managing BitLocker-protected volumes, and mounting Volume Shadow Copies. We are confident that Arsenal Image Mounter will be a great addition to your toolkit. Stay tuned for more updates!
Easily Launch Virtual Machines from Disk Images
Many Windows®-based disk image mounting solutions mount the contents of disk images as shares or partitions, rather than complete (aka “physical or “real”) disks, which limits their usefulness to digital forensics practitioners and others. Arsenal Image Mounter mounts the contents of disk images as complete disks in Windows, allowing users to benefit from disk-specific features like integration with Disk Manager, launching virtual machines (and then bypassing Windows authentication and DPAPI), managing BitLocker-protected volumes, mounting Volume Shadow Copies, and more.
Arsenal Image Mounter Features
Arsenal Image Mounter includes both free (Free Mode) and paid (Professional Mode) features.



