
Belkasoft
INCIDENT INVESTIGATIONS
Efficiently investigate hacking attempts of Windows computers
Overview
Belkasoft Incident Investigations is a part of Belkasoft X Corporate product. The module is developed specifically for businesses and aimed to investigate hacking attempts of Windows-based computers.
By analyzing numerous sources, you can identify traces that are typical of various techniques used by hackers to infiltrate a company’s infrastructure and base your cyber incident response on these findings.

Quick
Quickly respond to hacker attacks thanks to all necessary data conveniently presented on a single screen
Comprehensive analysis
Detect impactful security events by analyzing numerous sources, such as registry, event logs, other system files and less known sources
Search, bookmarking and reporting
Search inside found artifacts, bookmark important data and generate comprehensive incident reports right after the analysis stage
Compatibility with the other Belkasoft products
Benefit from the analytical capabilities of images acquired by Belkasoft R and Belkasoft T, as well as those obtained through third-party tools.
Affordable
Comparing to the pricing of the alternative products, it will fit your budget easily
Features
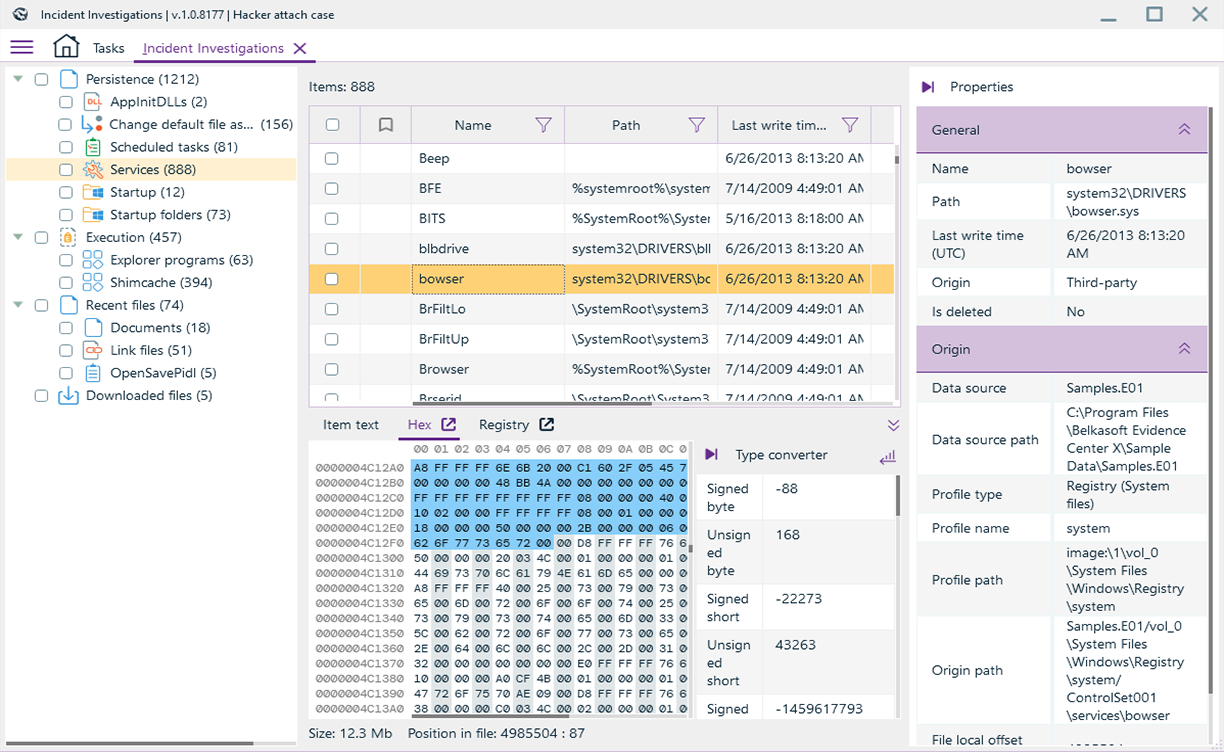
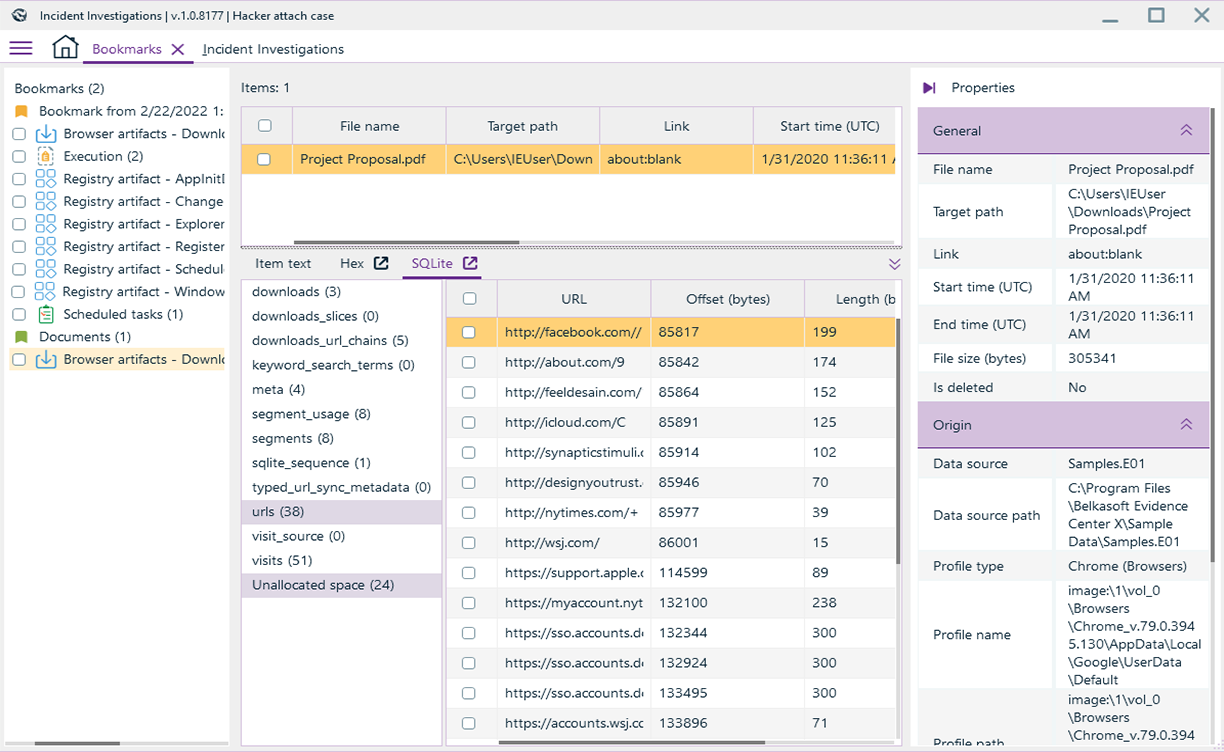
 Endpoint attacks
Endpoint attacks
Focus on attacks designed to compromise endpoints: phishing e-mails and other attack vectors begin with a compromised PC or laptop.
 Malicious email activity
Malicious email activity
Detect patterns indicating attackers use e-mail services to access the network.
 Remote access attacks
Remote access attacks
Detect misuse of remote access either by outsiders or insiders.
 Anomalous user activity
Anomalous user activity
Detect indications of abnormal system usage, abnormal use of credentials, or escalation of credentials.
 Attacks correlation with known vulnerabilities
Attacks correlation with known vulnerabilities
By means of consistent vulnerability scanning correlate attack vectors which can be utilized by malicious users to exploit those vulnerabilities.



