Capture Live RAM Contents with Free Tool from Belkasoft!
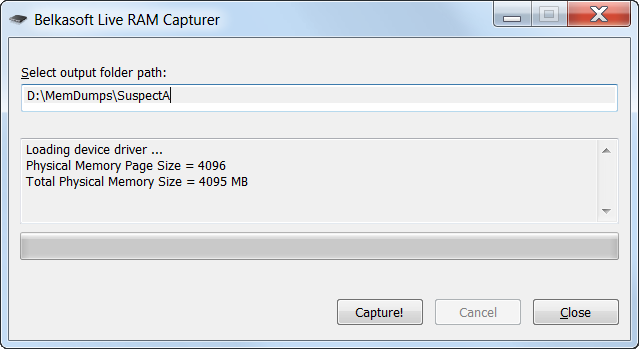
Belkasoft Live RAM Capturer is a tiny free forensic tool that allows to reliably extract the entire contents of computer’s volatile memory—even if protected by an active anti-debugging or anti-dumping system. Separate 32-bit and 64-bit builds are available in order to minimize the tool’s footprint as much as possible. Memory dumps captured with Belkasoft Live RAM Capturer can be analyzed with Live RAM Analysis in Belkasoft Evidence Center. Belkasoft Live RAM Capturer is compatible with all versions and editions of Windows including XP, Vista, Windows 7, 8 and 10, 2003 and 2008 Server.
Why Memory Dump Is the First Thing To Do During the Acquisition
Memory dumps are a valuable source of ephemeral evidence and volatile information. Memory dumps may contain passwords to encrypted volumes (TrueCrypt, BitLocker, PGP Disk), account login credentials for many webmail and social network services such as Gmail, Yahoo Mail, Hotmail, Facebook, Twitter; file sharing services such as Dropbox, Flickr, OneDrive, etc.
In order to extract ephemeral evidence out of already captured memory dumps, forensic experts must use proper analysis software such as Belkasoft X. Besides, some other tools can be used to extract passwords to encrypted volumes.
Designed to Bypass Active Anti-Debugging and Anti-Dumping Protection
Acquiring volatile memory from a computer running a debugging protection or anti-dumping system is tricky. Most memory acquisition tools run in the system’s user mode, and are unable to bypass the defense of such protection system (which run in the systems’ most privileged kernel mode).
Belkasoft Live RAM Capturer is designed to work correctly even if an aggressive anti-debugging or anti-memory dumping system is running. By operating in kernel mode, Belkasoft Live RAM Capturer plays on the same level with these protection systems, being able to correctly acquire address space of applications protected with the most sophisticated systems such as nProtect GameGuard.
Creates Forensically Sound Memory Dumps
Belkasoft Live RAM Capturer features the smallest footprint possible, does not require installation and can be launched in seconds from a USB flash drive. Unlike many competing tools running in system’s user mode, Belkasoft Live RAM Capturer comes equipped with 32-bit and 64-bit kernel drivers allowing the tool to operate in the most privileged kernel mode. Memory dumps acquired with Belkasoft Live RAM Capturer can be then analyzed with Belkasoft X.
Compared to Other Volatile Memory Capturing Tools
Belkasoft Live RAM Capturer beats many popular memory dumping applications hands down due to the difference in design goals. Current versions of competing tools (AccessData FTK Imager 3.0.0.1443, PMDump 1.2) operate in the system’s user mode, which makes them susceptible to anti-dumping activities performed by active debugging protection systems such as nProtect GameGuard.
An internal comparison between Belkasoft Live RAM Capturer and latest versions of competing RAM acquisition tools demonstrated the ability of Belkasoft Live RAM Capturer to acquire an image of a protected memory set while the other tools returned an empty area (FTK Imager) or random data (PMDump).
Tools tested:
- AccessData FTK Imager 3.0.0.1443
- PMDump 1.2
- Belkasoft Live RAM Capturer 1.0
Testing methodology: we launched Karos, a computer game protected with nProtect GameGuard. Then we performed an active chat session, and tried acquiring the complete memory dump of the system with all three memory dumping tools. We then analyzed the memory set belonging to the protected game.
The results:
- AccessData FTK Imager 3.0.0.1443 contained all zeroes in place of actual data for the protected memory set;
- PMDump 1.2 returned random data;
- Belkasoft Live RAM Capturer 1.0 correctly acquired the protected memory set.
Consequences of Using a Wrong Tool
Many applications protect their memory sets against dumping. Such applications include multi-player online games, malware, custom and commercial products protected with active anti-debugging systems. In mild scenarios (e.g. commercial products and games), an attempt to read a protected memory area will simply return empty or garbage data instead of the actual information.
In worst-case scenarios, an anti-debugging system detecting an attempt to read protected memory areas may take measures to destroy affected information and/or cause a kernel mode failure, locking up the computer and making further analysis impossible. This is what typically happens if a user-mode volatile memory analysis tool is used to dump content protected with a kernel-mode anti-debugging system.
Compatibility and System Requirements
Belkasoft Live RAM Capturer is compatible with 32-bit and 64-bit editions of Windows including XP, Vista, Windows 7/8/10/11, 2003 and 2008 Server. The tool does not require installation, and can be launched in seconds from a USB thumb drive.
Update
Since this article was published, FTK Imager got a kernel-mode driver. However, you may still consider to compare size of an executable file to select a capturer with minimum footprint. See a third-party review at https://thanursan.medium.com/comparison-of-memory-acquisition-software-for-windows-e8c6d981db23



