
Belkasoft
REMOTE ACQUISITION
Digital forensic and incident response tool developed specifically for remote extraction
Overview
Belkasoft Remote Acquisition (Belkasoft R) is a new tool developed specifically for remote extraction of hard and removable drives, RAM, connected mobile devices, and even specific types of data.
Belkasoft R will be useful in cases when an incident response analyst or a digital forensic investigator needs to gather evidence quickly and the devices in question are situated in geographically distributed locations.

EASY TO DEPLOY
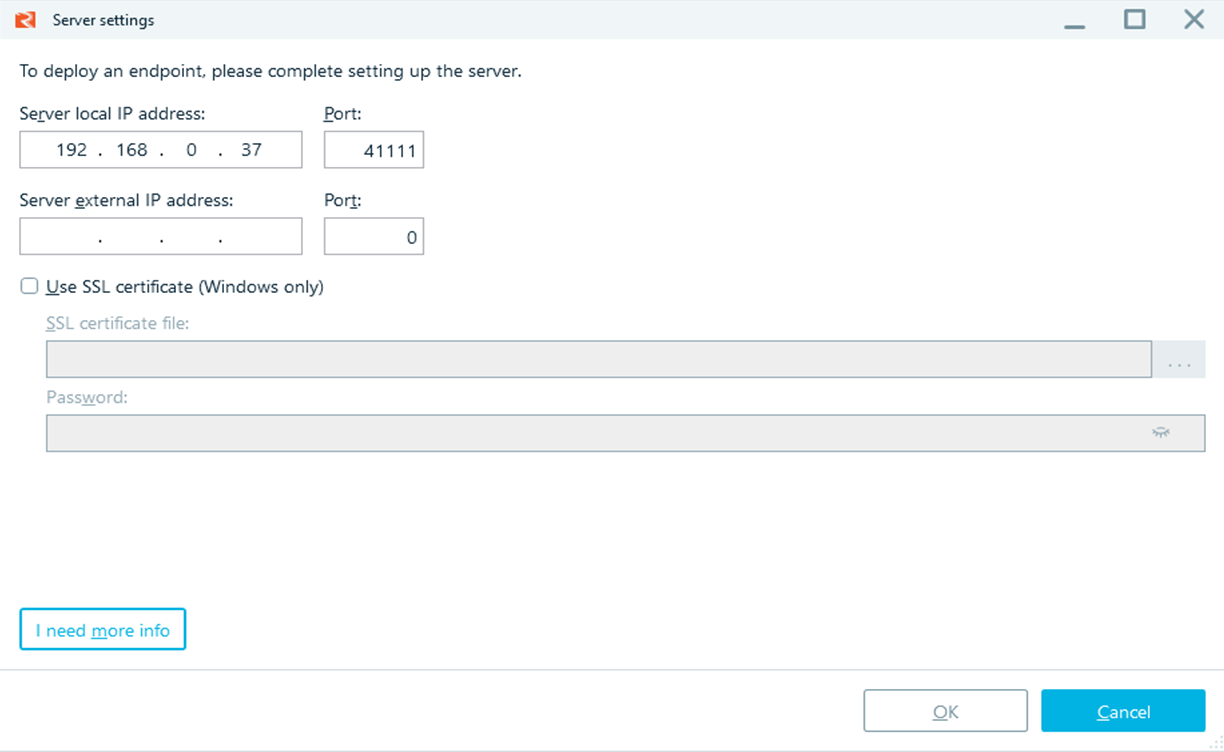
You can setup agent deployment over your network with a few mouse clicks using various deployment methods suAcquire the entire drive, RAM memory or select the artifacts crucial for your investigation. Upload the data immediately or choose the appropriate time.ch as GPO or WMI.
SUPPORT FOR VARIOUS OPERATING SYSTEMS
Select one or more endpoints and then select what evidence to acquire: whether you need a hard drive, volatile memory, mobile device or even specific types of data such as documents or pictures.
STRAIGHTFORWARD ACQUISITION
Acquire the entire drive, RAM memory or select the artifacts crucial for your investigation. Upload the data immediately or choose the appropriate time.
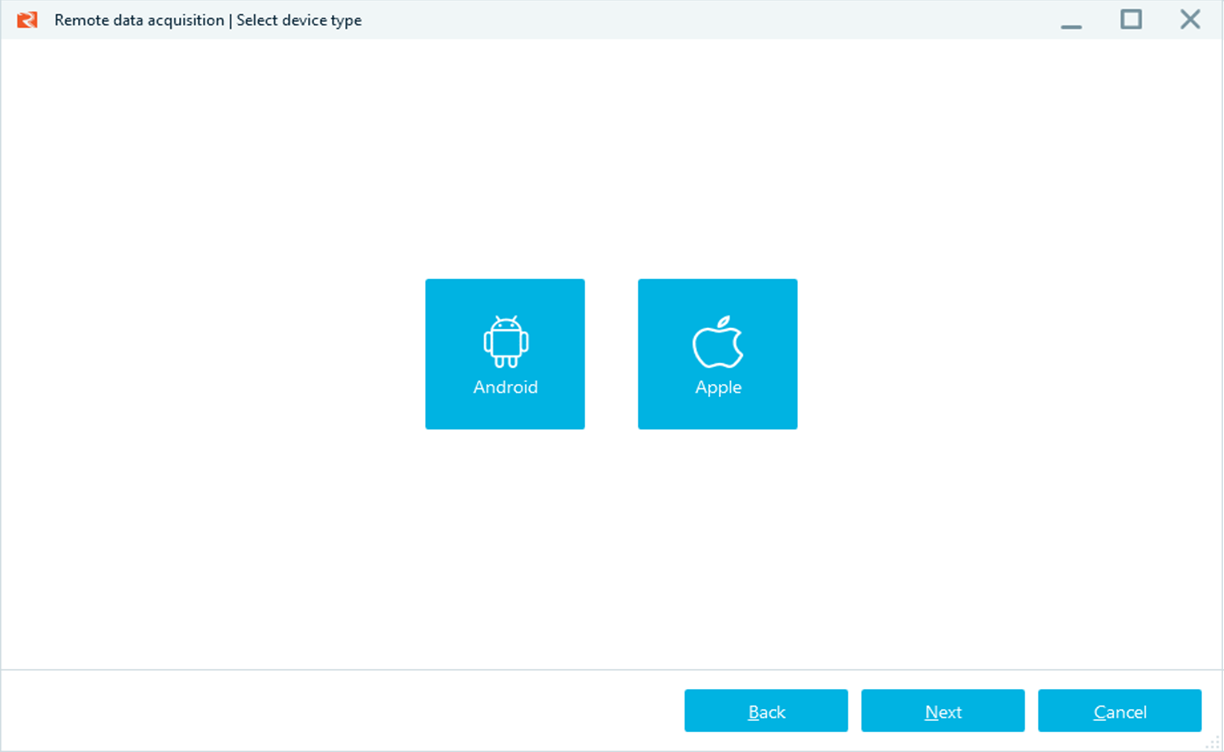
MOBILE DEVICE SUPPORT
Collect both iOS and Android mobile devices, located in other geographical areas!
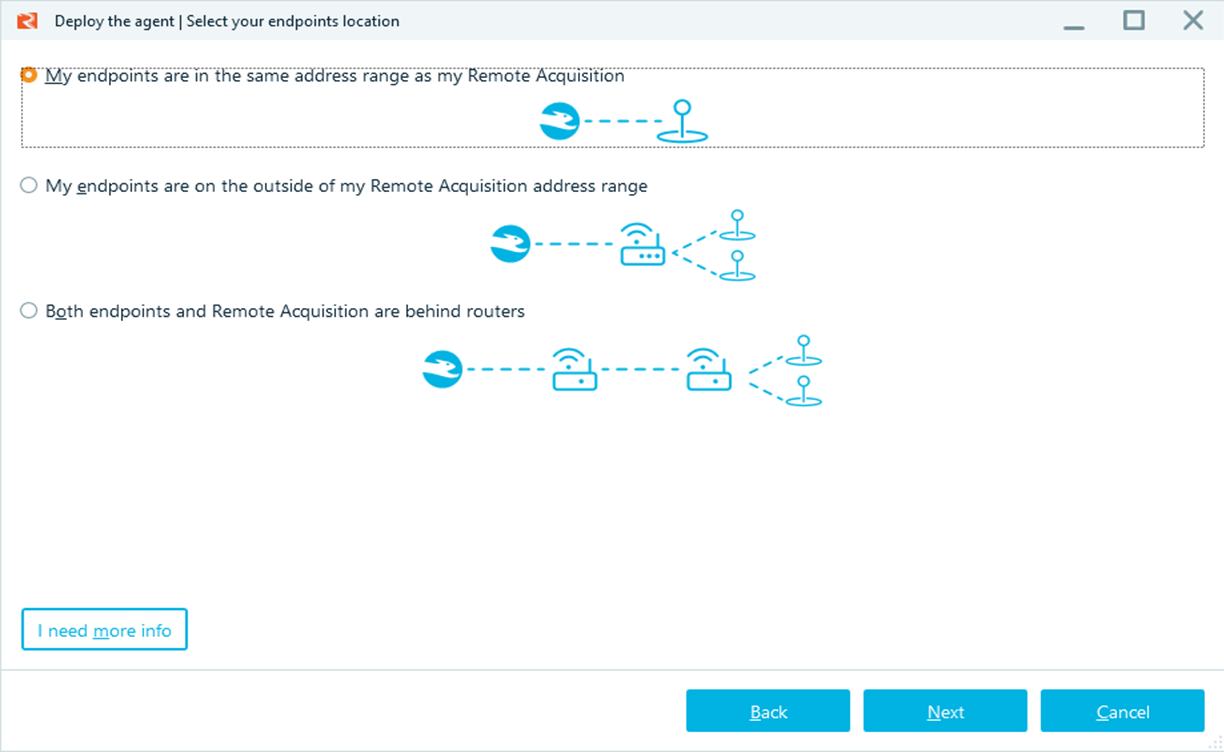
SUPPORT FOR VARIOUS NETWORK CONFIGURATIONS
Acquire endpoints from both local and global networks, including subnets behind routers, and access remote devices even on VPN.
QUICK PARTIAL ACQUISITION
In a hurry? Selective extraction of specific artifact types helps to save time by acquiring only necessary files.
MANAGE NETWORK BANDWIDTH WITH FLEXIBLE SCHEDULING
Belkasoft R allows you to specify acquisition time and upload time so that you can maintain your bandwidth load during working hours and schedule mass upload for the night time.
DO YOU HAVE A LARGE NETWORK?
Belkasoft R helps you to break-up your endpoints in multiple ways: by assigning them a name, group, location, and even a color, which can be used to manage various devices under your control. Easily edit or acquire endpoints from the same location or even by the same color!
Features
SUPPORTED ACQUISITION TYPES
DEPLOY AGENTS
SCHEDULE & ACQUIRE
Tutorials
How to start working with Belkasoft R
How to deploy an agent in Belkasoft R



