
Belkasoft
TRIAGE
Perform effective triage analysis of Windows devices right on the incident scene
Overview
Belkasoft T is designed to assist in situations when an investigator or a first responder is at the scene of incident and needs to quickly identify and obtain specific digital evidence stored on a Windows machine.
The product is irreplaceable in situations of time pressure, when there is a need to quickly detect presence of specific data and obtain investigative leads instead of conducting an in-depth analysis of all the digital evidence.
Easy-to-use
The product is user friendly enabling both experts and non-technical specialists to use it out of the box
No installation is required
Belkasoft T is portable and can be started from any thumb drive
Quick and smart
In a matter of minutes, you will get the information of presence of data you are looking for, such as, for instance, Skype profile or Outlook mailbox
Easy configuration
Belkasoft T can be easily configured during operation and does not require special knowledge to set up
Compatibility with Belkasoft X
Images acquired with Belkasoft T can be analyzed in Belkasoft X for a deeper insight into the content of the copied data
Now free!
Unleash the full potential of forensic triage analysis without breaking the bank, ensuring powerful tools are within reach for every investigator
Features
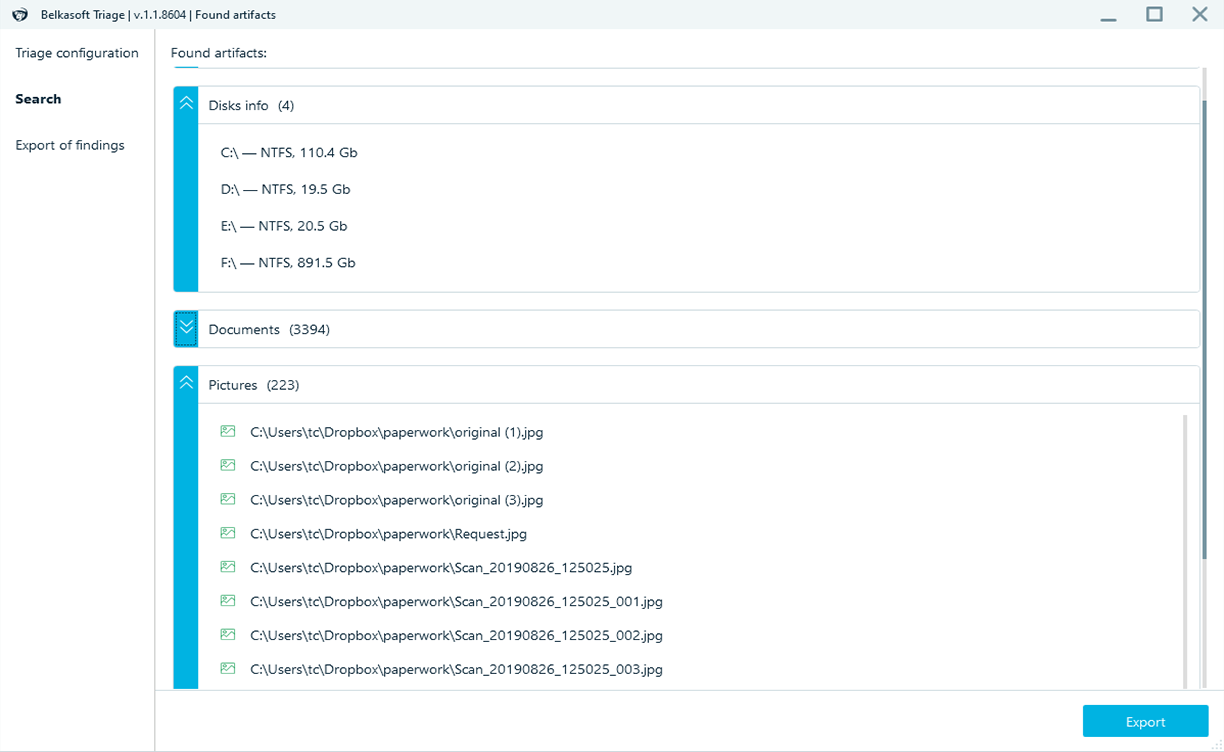
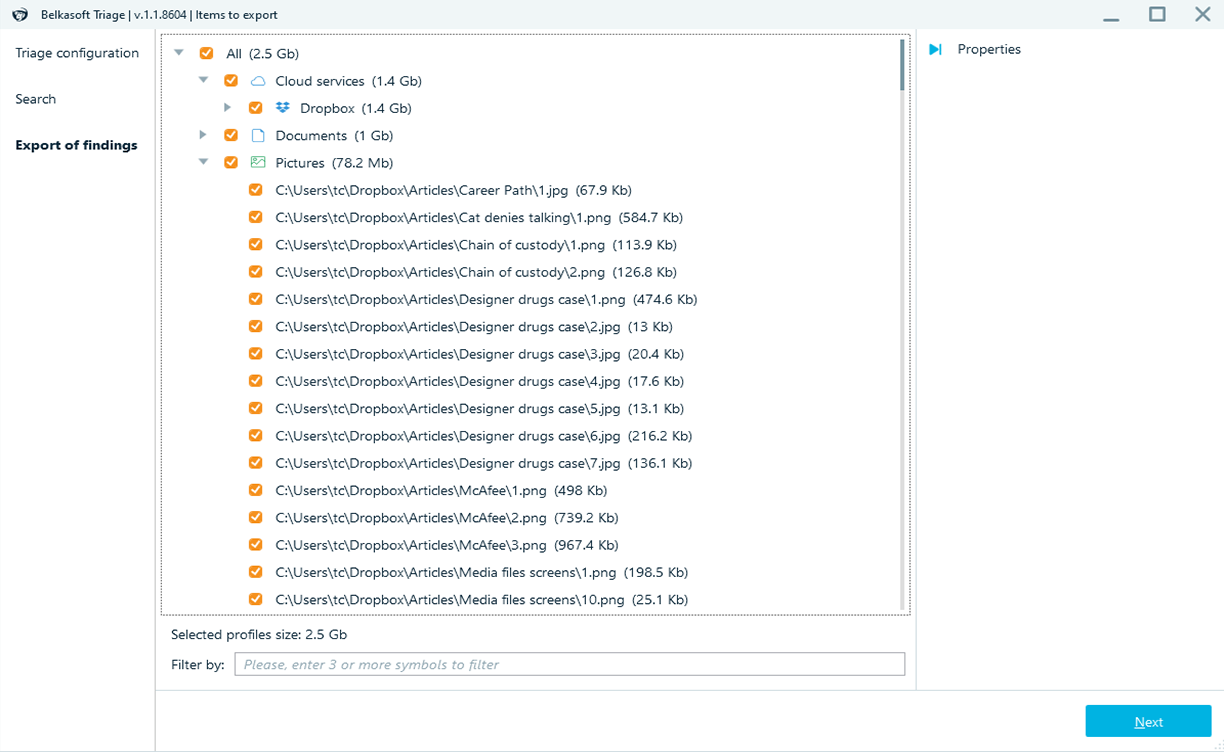
How it works
1. Run Belkasoft T from a thumb drive
2. Select a folder or disk. Acquire RAM if needed
3. Configure options, such as hash set databases and skin detection
4. Start the analysis and review the discovered application profiles
5. Export selected data into an image readable by Belkasoft X as well as other forensic tools



