Helix3 Enterprise is an easy to use cyber security solution integrated into your network giving you visibility across your entire infrastructure revealing malicious activities such as Internet abuse, data sharing and harassment. H3E also allows you to isolate and respond to incidents or threats quickly and without user detection through a central administration tool.
Helix3 Enterprise allows you to quickly Detect, Identify, Analyze, Preserve and Report giving you the evidence to reveal the truth and protect your business.
Helix3 Enterprise Features:
Easy to Use
Helix3 Enterprise is controlled through an easy to use graphical interface that works with any operating system. It is so easy it requires minimal to no training.
Quick Implementation
Installation is done quickly and can be pushed out through your network using your existing installation tools. Helix3 Enterprise will be running within the day!
Review Employee Internet Usage
Review an employee’s Internet usage history quickly, seeing what they searched for and what sites they visited.
Capture Screen Shots and Key Logging
With a simple click you can conduct a screen capture or key logging on any system within your network. You select the system you wish to monitor and choose Screen Capture from the menu to obtain what is on a system’s screen at any given time. Turn Key Logging on or off the same way, simply select the system then select the key logging option from the menu.
e-Discovery Across the Entire Network
With Helix3 Enterprise you can search your entire network for files with three different methods:
- Date and Time Stamps
- Keywords in file names, file content and regular expressions
- Hash values – for a more computer forensics method
Increasing legislation, especially Sarbanes-Oxley is causing problems for companies when e-discovery demands are made upon them. Our solution simplifies the issues by allowing Information Security personnel to search for defined data criteria, and either copy the data to a central location or report on its presence.
Sophisticated Computer Forensic Capabilities
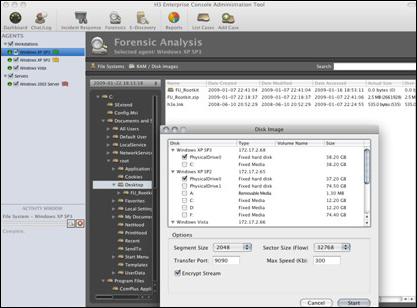
Helix3 Enterprise was developed by computer forensic experts and cyber crime investigators and built on the legendary Helix3. Collect forensic images of systems including RAM across multiple platforms, running processes, environment variables and much more!
Reporting
Reporting is an important part of any software application, your network security software is no different. You can pull concise reports on audits conducted and run Ad-hoc reports based on many different criteria.
Helix3 Enterprise Benefits:
Compliance Management
Implementation of network security software and procedures provide companies with the means to meet the requirements for compliance. Helix3 Enterprise is the solution every company needs!
Cyber Security
Cyber Security has become of great interest in recent years as more computers with sensitive or proprietary data are connected to the Internet and cyber crime is on the rise. There are many standards and good practices as outlined in ISO/IEC, COBIT, Standard of Good Practice and ITIL that advocate the importance of strong network security solutions. Helix3 Enterprise is that solution!
Protection from Employee Malicious Behavior
- Only 20% of Data Loss is Due to Hacking!
- 80% of Data Loss is Due to Internal Threats Including Employee Actions!
- The average incident due to hacking cost $67,000 (Deloitte)
- The average loss due to internal security breach is $2,300,000 (Deloitte)
- Government fines associated with lax security tend to be in the “seven figure” range.
- DATA SECURITY IS NOT AN OPTION TO THINK ABOUT AT A LATER DATE!
Helix3 Enterprise is a simple to use and powerful solution to secure your business! With H3E you have visibility across your entire infrastructure allowing you to isolate and respond to incidents or threats quickly!
Litigation Support
Today’s world is increasingly litigious. Companies find themselves in the middle of legal action and must be able to make data available quickly, usually from digital storage. Investigations like employee misconduct require e-discovery and computer forensics, in order to be successful. These requirements put pressure on already taxed IT Security teams. With Helix3 Enterprise incident response and e-discovery is handled correctly giving companies the evidence to revel the truth.
Information Security teams can manage their legal responsibilities from a central location using H3E ensuring computer forensic integrity of data. Computers in the enterprise can be examined, hard drives imaged for forensic examination and necessary surveillance carried out – from a central administration tool.
Intelligent Network Monitoring
Information Security personnel can monitor each computer or server on the network from a central administration tool when a tiny agent is installed. The agent allows the console to connect to it using encrypted authentication and provides the operator with the ability to collect volatile evidence, screenshots, key strokes, RAM – even the entire hard drive. The agent also provides abilities to monitor the computer for anomalous activity that can be set by the operator.
Cost Effective
Helix3 Enterprise is a cost-effective cyber security solution for any size business. Small offices to large enterprise companies can take advantage of this multi-faceted network security, computer forensics and e-discovery solution!