Forensic Email Intelligence™
Experts’ choice for investigating email fraud, business email compromise (BEC), malware delivery, and CAN-SPAM Act violations.
In-place Decoding and Assistance
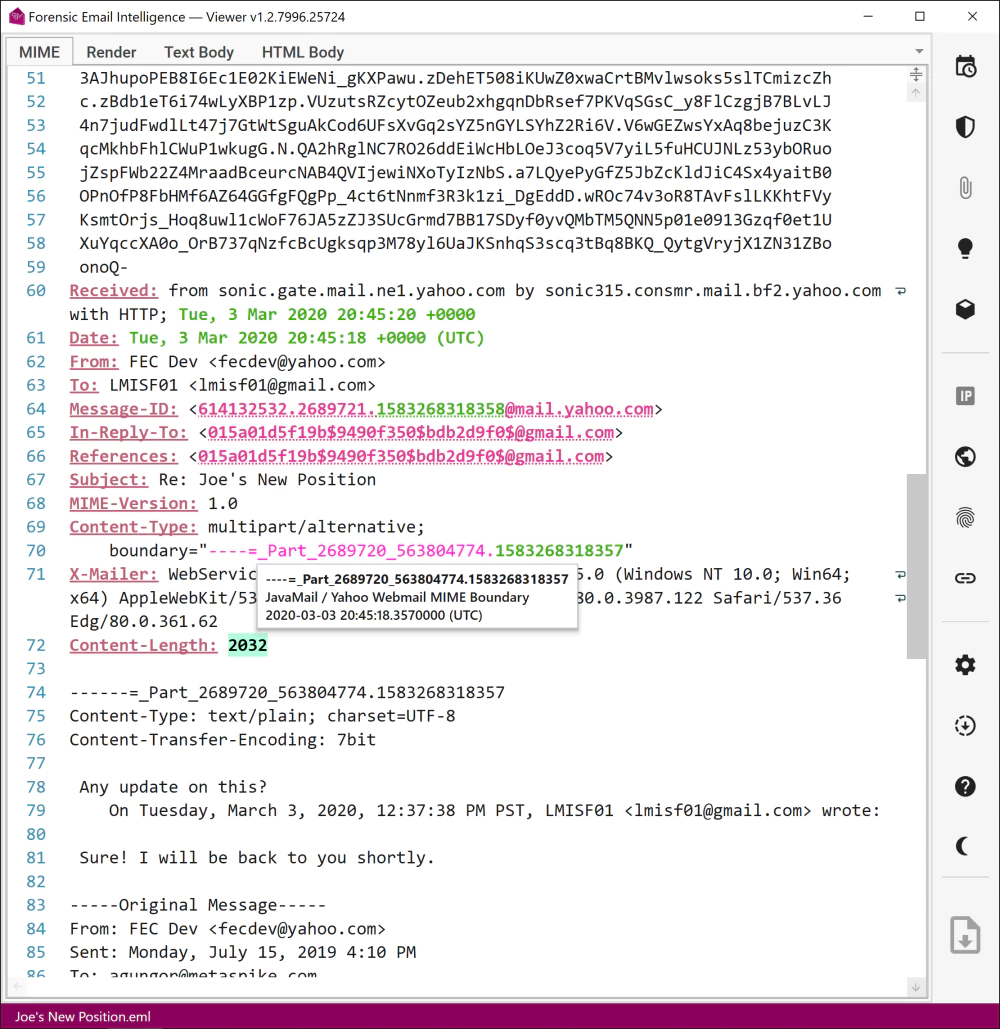
Feel like looking for a needle in a haystack? Forensic Email Intelligence automatically highlights and identifies MIME headers and provides helpful description snippets.
In addition, cryptic artifacts such as hidden timestamps in MIME boundary delimiters and Message-IDs are decoded on the fly so that crucial evidence doesn’t go unnoticed.
DKIM & ARC Verification
Verification of DomainKeys Identified Mail (DKIM) and Authenticated Received Chain (ARC) signatures is a fundamental step in email forensics. Forensic Email Intelligence takes care of the hard work for you by fetching the public keys, calculating the header and body hashes, and verifying both the ARC chain and DKIM—multiple signatures are supported if available.
Encountered a suspicious signing domain? You can head over to FEI’s domain intelligence view to learn all about it!
Automated Timelining
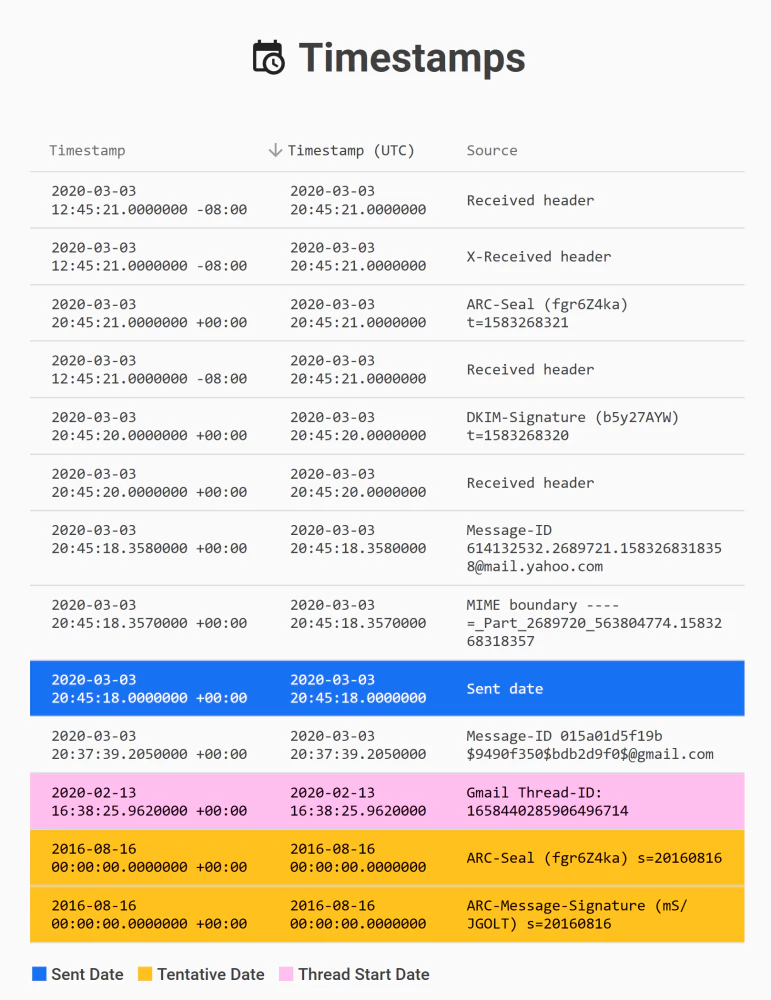
One of the first steps email examiners take when analyzing a message is to create a timeline. The timeline should include all timestamps encountered in the email, such as MIME headers, MAPI properties, file system timestamps of attachments, hidden timestamps, thread index timestamps, and more.
Forensic Email Intelligence makes this time-consuming task a breeze! At the click of a button, you have a sortable overview of the original timestamps, their UTC-normalized version, and a description of where each timestamp was found!
Insights and Scoring
Wouldn’t it be great if your forensic tools went beyond displaying raw data and offered insights? Forensic Email Intelligence goes a step further and scores emails on how likely they are to be fraudulent.
Insights include a detailed description of inconsistencies among the data points within a message and details such as what email client was likely used to compose it and which email service provider was likely involved in the transfer.
MAPI Inspection
Messaging Application Programming Interface (MAPI) provides a treasure trove of information when examining Microsoft Outlook messages and data stores. Forensic Email Intelligence takes MAPI properties into account while scoring emails and offering insights and allows direct inspection of the underlying MAPI properties.
Using FEI’s built-in tools, you can rapidly search and filter MAPI properties and utilize them in your investigation.

API Integrations for Enrichment
Interested in where an IP address is located or if it belongs to a VPN service? How about historical mail exchanger (MX) records of a domain or a list of its subdomains?
Forensic Email Intelligence connects to external APIs such as MaxMind, SecurityTrails, and EmailRep to enrich data points and give you the full scope!



