OpenText EnCase Endpoint Security
Detect, analyze, triage and respond to malicious attacks with complete endpoint visibility
99%
of detections are made in real-time with EnCase Endpoint Security
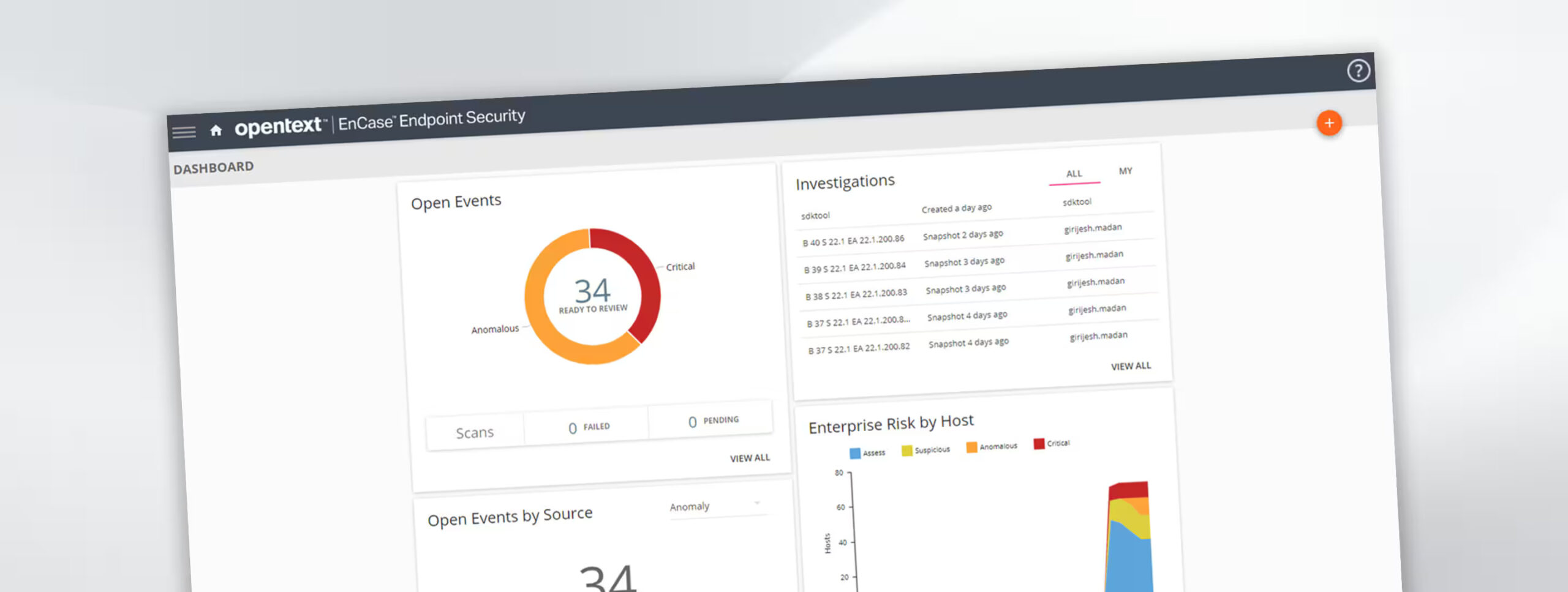
OpenText™ EnCase™ Endpoint Security, a leading endpoint detection and response (EDR) solution, empowers security analysts to quickly detect, validate, analyze, triage and respond to incidents. EnCase Endpoint Security comprehensively tackles the most advanced endpoint attacks, whether from internal or external threats.
Why choose OpenText EnCase Endpoint Security?
-
Comprehensive detection and recovery
Instantly detect and take action against threats with the most comprehensive, context-driven response and recovery.
-
Industry-leading endpoint visibility
Comprehensively detect advanced malware, insider activity and other threats across hybrid and remote workforces.
-
Powerful flexibility and configuration
Easily adapt and customize detection rules and stay ahead of the latest tactics, techniques and procedures (TTPs).
How EnCase Endpoint Security can benefit your business
Discover the advantages of using EnCase Endpoint Security
-
Boost threat detection
Confidently detect the latest threats with regularly updated, pre-filtered detection rules based on the MITRE ATT&CK™ framework.
-
Quickly identify root causes
Create event timelines and use other threat-hunting capabilities to drive root-cause analysis and fully understand the extent and nature of any compromise.
-
Empower response teams
Accelerate incident-response teams’ ability to validate, assess and remediate malicious activity, reducing triage time by up to 90 percent.
-
Rely on a proven endpoint agent
Maximize visibility and support for the broadest range of operating systems to gain insights regardless of the underlying OS.
Features
-
Continuous endpoint monitoring
Uncovers cyber threats enterprise-wide with real-time, behavior-based detections, inspired by industry-leading frameworks, such as MITRE ATT&CK.
-
Orchestrated workflows and operations
Integrates with third-party security solutions through open, documented RESTful APIs to optimize security operations and automate workflows.
-
Integrated threat intelligence
Automatically prioritizes alerts by severity, leveraging BrightCloud® Threat Intelligence to complete file and IP reputation analyses and display results in a single view.
-
Powerful remediation
Enables users to wipe malicious files, kill processes, reset Registry keys and isolate affected endpoints while allowing response activities to continue.
-
Advanced agent anti-tampering
Deploys the latest anti-tampering capabilities to defend against malicious attacks and prevent agents from being disabled or otherwise manipulated.