
Digital investigations for a new era
For Windows
- Identify suspicious files and activity.
- Extract evidence from computers quickly.
- Manage your investigation.
Complete suite for forensic investigation
Search files fast
OSF provides one of the fastest and most powerful ways to locate files on a Windows computer or Forensic image. Learn more
Search within the contents of files with the use of our acclaimed indexing engine providing industry leading relevance ranking, date range searching, exact phrase matching, “Google-like” context results and more.

Extensive file type support
Investigate and search within hundreds of file types including Office and Acrobat documents, image files (with OCR), e-mails (Outlook, Thunderbird, Mozilla and more), attachments, ZIP files, and even binary files and unallocated clusters. Learn more
Recover deleted evidence
Search and recover files that a user may have attempted to destroy or have been removed from the Recycle Bin. Learn more

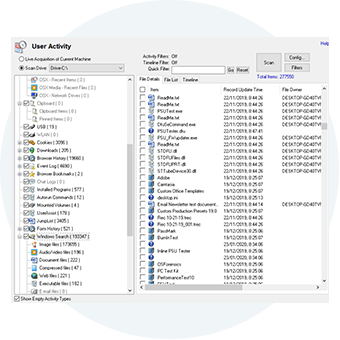
Uncover user activity
Scan the computer for evidence of recent activity, including accessed websites, USB drives that have been connected, wireless networks, recent downloads, website logins and website passwords. Learn more
Password recovery
OSF provide powerful tools to uncover and crack passwords on a live system or forensic image. These include:
- Web site logins and passwords (used in Chrome, Edge, IE, Firefox and Opera)
- Outlook and Windows Live passwords
- Saved Wifi passwords
- Windows autologon password
- Windows and other Microsoft product keys
- Ports (Serial/Parallel)
- Network adapters
- Physical and optical drives
- Bitlocker detection
OSF also provide tools to crack hashes with the use of rainbow tables, and dictionary attacks. Learn more.
Reveal hidden areas on a hard disk
OSF can expose the HPA and DCO hidden areas of a hard disk which can be used for malicious intent, including hiding illegal data. Learn more

Browse Volume Shadow copies
Use OSF to access Volume Shadow Copies. This allows you to look at how a disk appeared at a point of in time in the past and see what has changed. Discover changes to files and even view deleted files. Learn more

Identify suspicious files and activity
Verify and match files
Use OSF to confirm that files have not been corrupted or tampered with by comparing hash values or identify whether an unknown file belongs to a known set of files. Verify and match files with MD5, SHA-1 and SHA-256 hashes. Find misnamed files where the contents don’t match their extension. Learn more

Identify changes
Create and compare drive signatures to identify differences and changes made on a system. OSF lets you create a forensic signature of a hard disk drive, preserving information about file and directory structures present on the system at the time of signature creation. Learn more
Timeline viewer
OSF features a Timeline Viewer that provides a visual representation of file and system activity over time, helping you to identify date ranges where significant activity has occurred, or build up a pattern of behavior over years, months or days. Learn more
File analysis tools
OSF provides a comprehensive suite of tools to analyze files, emails, and system information including:
- File viewer that can display streams, hex, text, images and meta data
- Email viewer that can display messages directly from the archive
- Registry viewer to allow easy access to Windows registry hive files
- File system browser for explorer-like navigation of supported file systems on physical drives, volumes and images
- Raw disk viewer to navigate and search through the raw disk bytes on physical drives, volumes and images
- Web browser to browse and capture online content for offline evidence management
- ThumbCache viewer to browse ThumbCache viewer to browse the Windows thumbnail cache database for evidence of images/files that may have once been in the system
- SQLite database browser to view the and analyze the contents of SQLite database files
- ESEDB viewer to view and analyze the contents of ESE DB (.edb) database files, a common storage format used by various Microsoft applications
- Prefetch viewer to identify the time and frequency of applications that been running on the system, and thus recorded by the O/S’s Prefetcher
- Plist viewer to view the contents of Plist files commonly used by MacOS, OSX, and iOS to store settings
- $UsnJrnl viewer to view the entries stored in the USN Journal which is used by NTFS to track changes to the volume
Manage your digital investigation
Create case
Organize all the evidence you have discovered into a single, cryptographically secure case file. Learn more

Generate Report
Export your case file as an accessible and customizable report showing all evidence associated with the case. Deliver a readable summary of forensic findings to clients or law enforcement agents at any point in your investigation. Learn more
Storage device management
Manage your storage devices in a centralized manner for convenient access throughout OSF. Learn more

Drive and system imaging
Create and restore disk images of evidence disks, to support forensics analysis without risking the integrity of the original data. Learn more
Rebuild a complete RAID image from a set of RAID member disk images. Learn more
Make exact copies of the partitions or drives of an active system. Useful for live acquisitions while running OSF from your USB drive. Learn more
Audit trace
OSF can automatically maintain a secure audit trail of the exact activities carried out during the course of the investigation. Learn more
Take OSF with you
OSForensics can be installed and run from a portable USB drive. Take the investigation straight to the target computer without risking the contamination of valuable forensic information. Learn more

Professional and Bootable Editions
The professional and bootable editions of OSForensics have many features not available in the free edition, including;
- Import and export of hash sets
- Customizable system information gathering
- No limits on the amount of cases being managed through OSForensics
- Restoration of multiple deleted files in one operation
- List and search for alternate file streams
- Sort image files by colour
- Disk indexing and searching not restricted to a fixed number of files
- No watermark on web captures
- Multi-core acceleration for file decryption
- Customizable System Information Gathering
- View NTFS directory $I30 entries to identify potential hidden/deleted files
- Memory viewer and dumper – Kernel mode acquisition to bypass anti-dump tools
The bootable edition contains all the professional features plus the ability to be run on systems without a valid operating system. See the full comparison list between the editions.
Free Tools
The following collection of tools are provided as free downloads for use with OSForensics™.
OSFMount
OSFMount allows you to mount local disk image files in Windows as a physical disk or a logical drive letter.
OSFClone
OSFClone enables you to create or clone exact raw disk images quickly and independent of the installed operating system.
Volatility Workbench
Volatility Workbench is a graphical user interface (GUI) for the Volatility tool.
ImageUSB
ImageUSB is a free utility which lets you write an image concurrently to multiple USB Flash Drives.



